APSB08-15 is the latest adobe security advisory regarding a memory corruption vulnerabilty in Acrobat Reader versions <8.1.2
As expected, the advisory does not include technical details about the attack vector, So let’s try to reverse the related Adobe patch to find more about this vulnerability. I’m going to use IDA 5.2 with patchdiff2 plugin (thanks to kris hint on this plug-in).
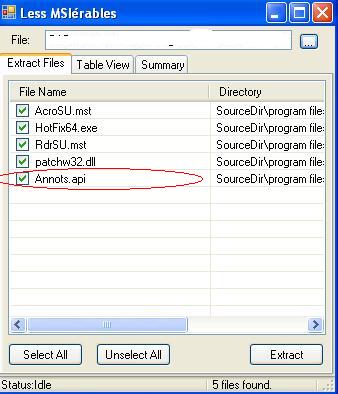
The patch is released as a MSI file. I used Greg Duncan’s Less MSIèrables tool to examine the content of this patch:
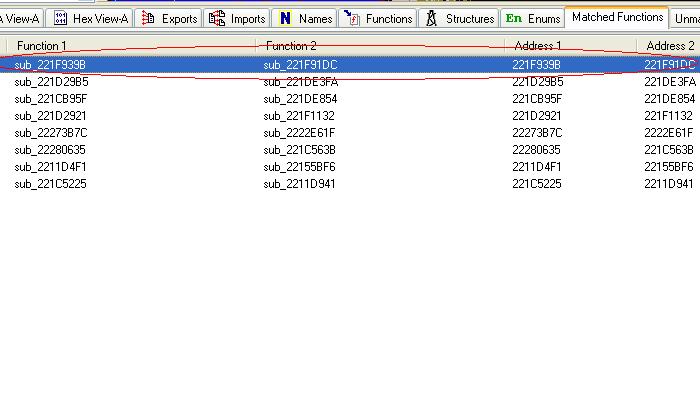
Adobe has just updated the annots.api plugin file, so I should just build the IDA Database files for the old and updated annots.api files and pathdiff them. Eight matched functions in the results:
By getting the Xrefs of the first matched function and backtracing it, we get into the VTABLE setup routine for a method named “collectEmailInfo” of “Collab” object. There was nothing in Adobe JavaScript guide for this method, so by googling and reading the function code I got the below syntax:
doc.Collab.collectEmailInfo({to:”to addr”,cc:”cc”,bcc:”bcc”,subj:”subject”,msg:”msg body”,…});
msg parameter seems to be a good candidate to overflow. Let’s make a PDF file with the below javascript embedded in and test it:
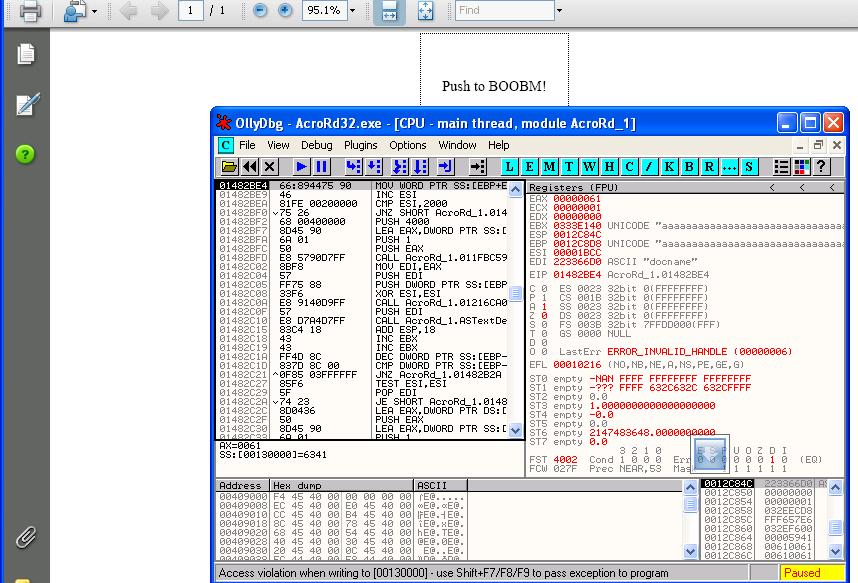
Collab.collectEmailInfo({msg:”aaaaaa…..aaaaa”}); (32K of aaa in my case)
and here is the result:
the place where the access violation occurs was different from machine,os,state , so the chance of the successful exploitation via heap spray is low.
/behrang