When performing spear phishing attacks, the more information you have at your disposal, the better. One tactic we thought useful was this Skype security flaw disclosed in the early days of 2012 (discovered by one of the Skype engineers much earlier).
For those who haven’t heard of it – this vulnerability allows an attacker to passively disclose victims external, as well as internal, IP addresses in a matter of seconds, by viewing the victims VCard through an ‘Add Contact’ form.
Why is this useful?
1. Verifying the identity and the location of the target contact. Great when performing geo-targeted phishing attacks.
2. Checking whether your Skype account has not been used elsewhere :)
3. Spear phishing enumeration while Pen Testing.
4. Just out of plain curiosity.
To get this working, following these basic steps:
1. Download and install the patched version of Skype 5.5 from here (the patch enables the Skype client to save the logs in non obfuscated form)
2. Save the lines below as a Skype_log_patch.reg reg file:
Windows Registry Editor Version 5.00[HKEY_CURRENT_USER\Software\Skype\Phone\UI\General]“LastLanguage”=”en”“Logging”=”SkypeDebug2003”“Logging2″=”on”
Once saved, run it to enable the Skype Debug Log File.
4. Start Skype.
5. Search for any Skype contact and click on the ‘Add a Skype Contact’ button, but do not send the request, rather click on the user to view their VCard.
4. Open the log file (it should appear in the same folder as Skype executable e.g. debug-20121003-0150)
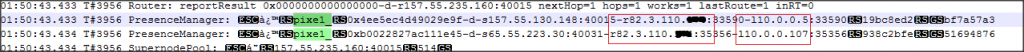
5. Look for the PresenceManager line – you should see something similar to this – >
In the above image you can spot my Skype name, external as well as internal IP addresses.
The log will include similar credentials for everyone listed as a “contact” under your Skype account, as well as many other fresh, genuine and useful information received directly from your local Skype tracker.